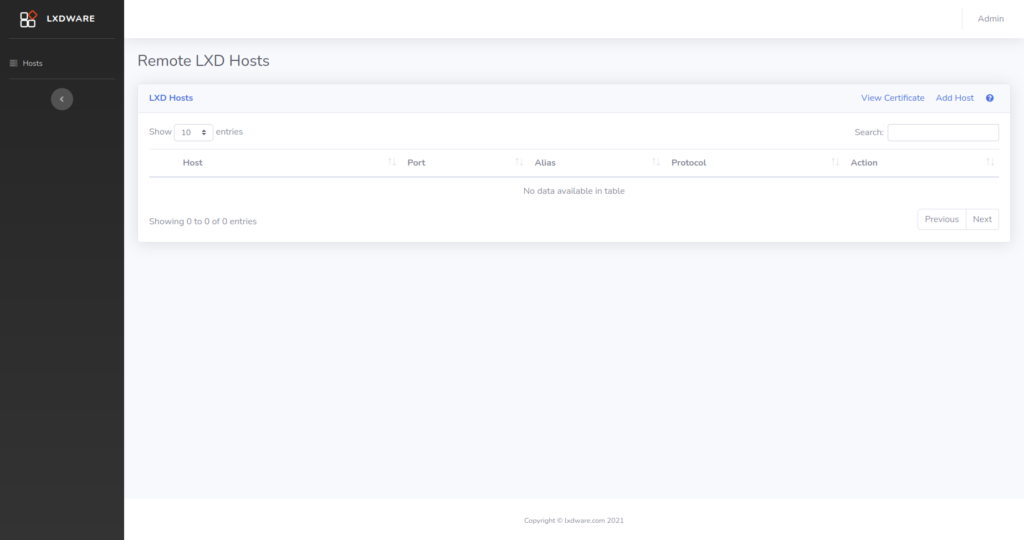
LXDWARE is excited to announce the 2.0.0 release of the LXD dashboard. This new release adds a lot of changes to the underlying code and improvements to the user experience. The LXD dashboard can now be deployed centrally within a network and allows multiple users to connect and manage LXD infrastructure through a single interface.
When deploying a new installation or upgrading from version 1.2.8, a registration page will first be presented to configure the default admin account. Database tables will automatically be converted to support new features when upgrading from version 1.2.8. The installation process has become much simpler, removing the need for most of the configuration. Some dependency packages have been replaced and installation guides have been updated for this release at https://lxdware.com/installation/
User accounts
Past versions of the dashboard used http basic authentication for password protecting the dashboard. This method worked great for a single-user application, but this new release now supports multiple user accounts. The authentication method now stores user accounts in a database and utilizes PHP Session variables. User account password hashes are no longer generated using the Apache htpasswd application, as hashes are now stored using the secure bcrypt hashing algorithm.
RBAC
The LXD dashboard now also supports the use of groups and role-based access control (RBAC). There are 4 default roles that can be assigned to user groups: ADMIN, OPERATOR, USER, and AUDITOR. The ADMIN role gives access to all controls with the system. The OPERATOR roles give access to all controls used to make changes to LXD servers. The USER role gives access to controls used in basic lifecycle commands of an instance. The AUDITOR role acts as a guest or read-only account giving access to controls that only display LXD resources.
Console Terminal
The Exec option has been replaced with a more robust console terminal. Using xterm.js and web sockets, users can connect to the console of both container and virtual machine instances. This new console emulates the feel of being directly connected to the instance. To login to instances, a user account and password will need to be configured in the virtual instances.
Network ACLs
Network ACLs are now a part of the LXD dashboard. Users can create new access control lists (ACLs) as well as modify their ingress and egress rules.
Certificates
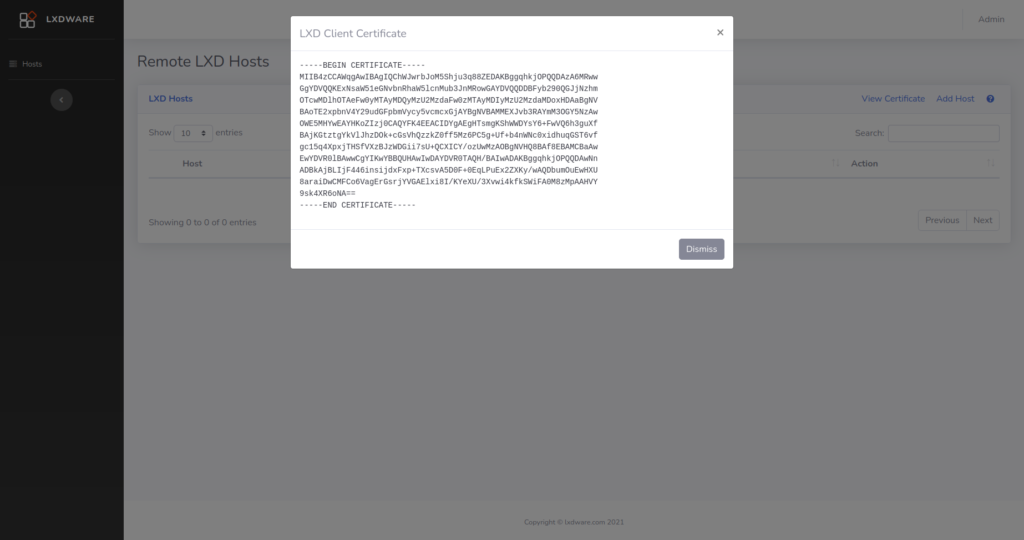
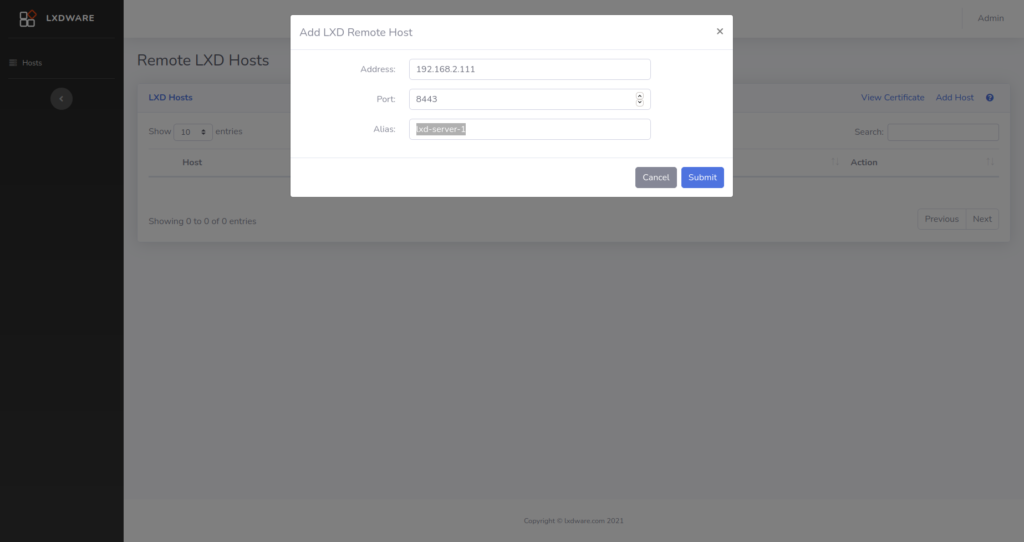
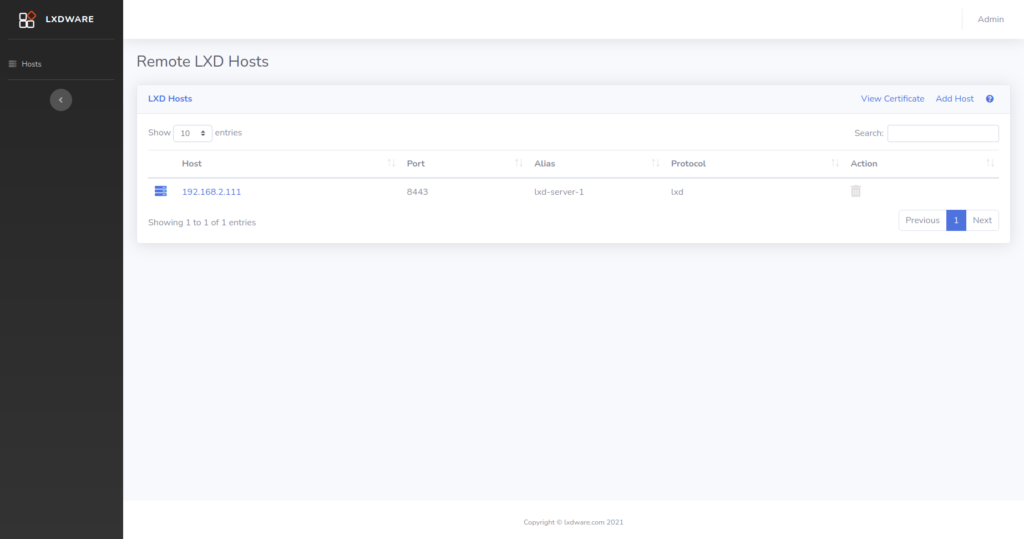
Previous versions of the dashboard relied on using a compiled LXC binary for generating LXC certificates. Certificates are now created using the built-in OpenSSL libraries within PHP. This allows the application to create certificates as needed rather than relying on users first creating their own certificates when installing the dashboard. Also now through the dashboard interface, users can add additional trusted certificates to a remote LXD host.
Curl
Curl connections made to the REST API of remote LXD servers are now made using PHP’s curl implementation rather than using the installed curl application on the host operating system. Changes no longer have to be made to the /etc/sudoers file, helping to reduce configuration problems and improve security. Now all a user has to do is just install the php-curl package on dashboard host system.
Database
Tables are now created automatically from within the dashboard rather than having to manually create them before installation. Database connections now use PDO statements allowing for consistent SQL statements between additional database systems, which are planned for future releases of the application.
Local Web assets
The LXD dashboard uses Google fonts for the web pages. Changes have been made to now use these fonts locally within the application rather than pulling them down from the Internet. All web assets are included within the application allowing the dashboard to work flawlessly within secure isolated network environments.
Accounting
Support is now built into this release of the application to log all controlled events. This logging of events to the database is planned in a future release of the application.